
Services Overview
Maximize the value of your mission-critical technology ecosystem
Test Marketing Notification Banner Test - Marketing Notification Banner. Read more info Join test helo specify single pages or pages under specific
Routines or disasters, your technology must be ready. Our mission-critical rigor to people, process & tools centralizes operations so you can manage your mission.
Prince George’s County enables efficient and smooth communication operations so its public safety agencies can focus on serving their communities.
Infrastructure Services
Address complex technology management with proactive and predictive services.
Device Services
Optimize fleet performance with device programming services and analytics.
Software Services
Experience uninterrupted command center operations with on-prem, hybrid and cloud-based software solutions.
Video Services
Protect your 'eyes on scene' with video security infrastructure & application services.
Cybersecurity Services
Identify, protect and prevent cyber threats with cybersecurity services.
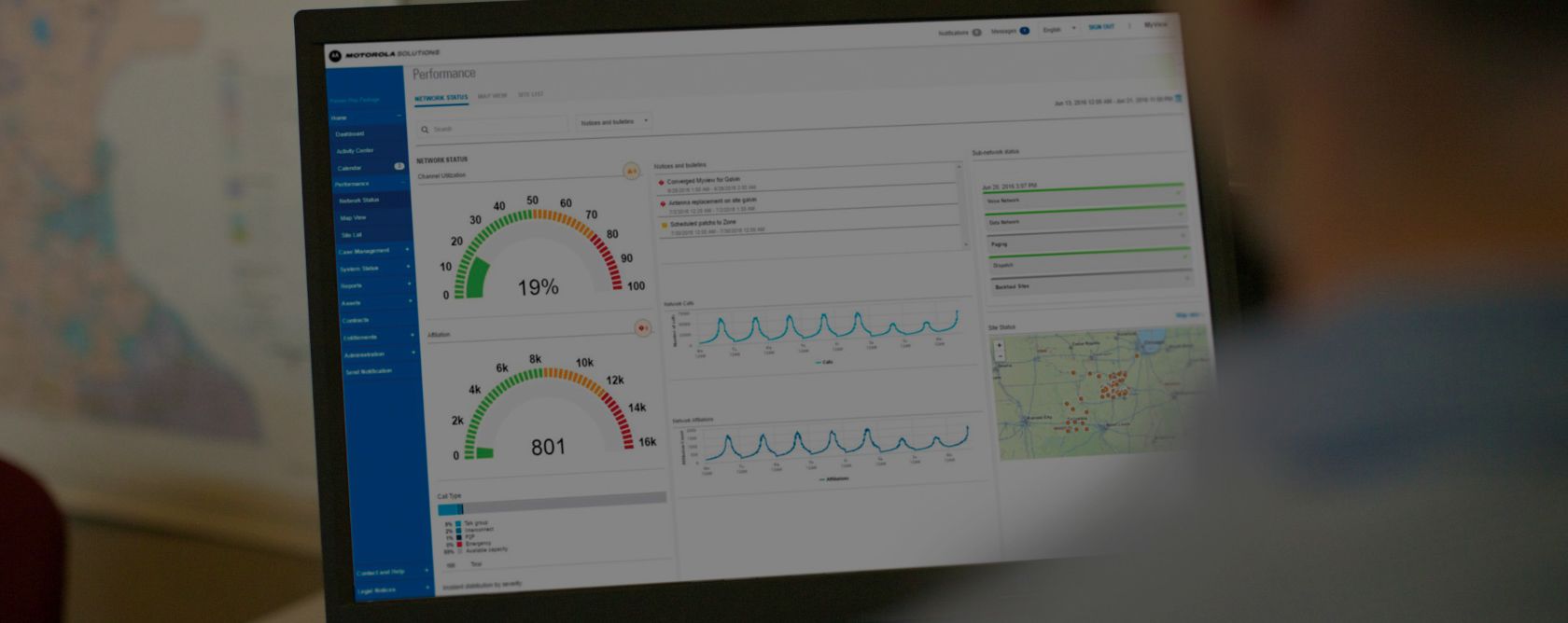
Mitigate risk and enhance system performance with MyView Portal’s customizable insights and dashboards.
Essential services
Technical support when and where you need it, so you can maintain and restore your system.
Advanced services
Rely on us to monitor and update your system, providing improved response and continuity.
Premier services
Transfer day-to-day accountability to us to operate and optimize your system to maximize performance and reduce risk.
Land Mobile
Radio
Stay safe and connected with the most advanced and reliable radios.
Public Safety
LTE
Put real-time data and video in the hands of first responders.
Command Center Software Suite
Streamline operations with the only end-to-end public safety software suite.
Video Security
& Analytics
Detect and deter crime through video security and self-learning video analytics.
Managed & Support Services
Deliver mission-critical operations so your team’s lifeline is always ready.
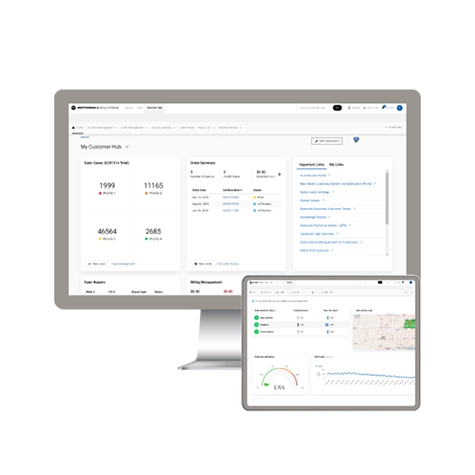
Track cases, see and update case management details, submit repair requests and much more.
With the widespread adoption of web applications, mobile applications and cloud-based environments, the network perimeter as we once knew it has changed. All it takes is one software defect or misconfiguration for cyber criminals to get a foothold in your environment and steal or compromise valuable information and assets. Vulnerability assessments and network scansup
Please wait...
Please wait...